Set up Slack notifications for detected issues in STO
This topic describes how to generate Slack notifications for STO-related events such as:
- A scan detected new vulnerabilities.
- A scan detected critical- or high-severity vulnerabilities.
- A scan step failed because it crossed my Fail on Severity threshold or violated one or more of my OPA policies.
To set up Slack notifications, you add a simple script to your pipeline that does the following:
-
Determines whether to send a notification.
-
Creates a string variable with your notification content.
-
Posts the notification to your Slack webhook.
Before you begin
-
Add an incoming webhook to your Slack app.
-
Run a cURL command to verify that you can post notifications to the webhook.
For information about these steps, go to Sending messages using incoming webhooks in the Slack documentation.
-
Create a Harness secret for your webhook URL.
Add the script to your pipeline
-
In your scan stage, add a Run step after the scan step.
-
Set the shell type. This example workflow uses Bash.
-
If you want to send a Slack when the scan step fails, add a failure strategy to ignore the failure for all errors.
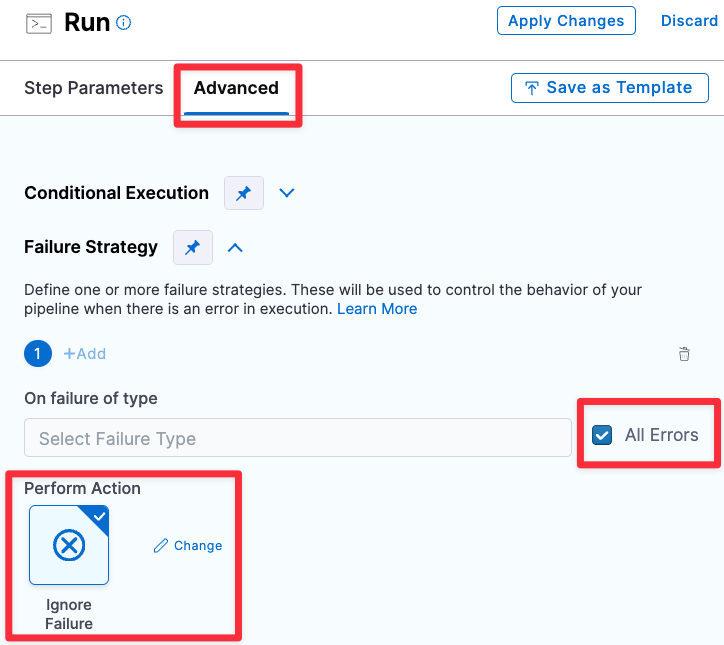
-
Set up your script as follows.
Add variables for your pipeline and scan results
This is optional but can make your script easier to understand and update.
Here's an example:
pipeline_url="YOUR_HARNESS_PIPELINE_URL"
new_critical="<+pipeline.stages.YOUR_SCAN_STAGE.spec.execution.steps.YOUR_SCAN_STEP.output.outputVariables.NEW_CRITICAL>"
new_high="<+pipeline.stages.YOUR_SCAN_STAGE.spec.execution.steps.YOUR_SCAN_STEP.output.outputVariables.NEW_HIGH>"
To get the full expression for an output variable:
-
Go to the Pipeline Execution page for a previous run of your STO pipeline.
-
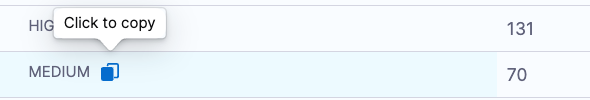
Navigate to Pipeline > scan_stage_id > Output.
-
Hover next to the variable name to access Click to Copy.
Send the notification?
If you want to send notifications based on your scan results, check the output variables from the previous scan step. If all the variables you're interested in are zero, there's no need to send a notification.
issues_total=$(( $new_critical + $new_high))
if [ "$issues_total" == "0" ]; then
exit 0
fi
Generate the notification content
Create a string variable for your notification content. Include the pipeline URL, the scan output, and any other relevant information. For example:
slack_msg="======================================================= \n"
slack_msg="$slack_msg WARNING: New vulnerabilities detected with severity CRITICAL or HIGH. \n"
slack_msg="$slack_msg $pipeline_url \n"
slack_msg="$slack_msg - NEW_CRITICAL issues: \t $new_critical \n"
slack_msg="$slack_msg - NEW_HIGH issues: \t = $new_high \n"
slack_msg="$slack_msg ======================================================= \n"
Post the notification
Add a cURL command to post the notification to your Slack webhook. In this example, $slack_hook is the Harness secret for the Slack webhook URL.
curl -X POST --data-urlencode "payload={
\"channel\": \"YOUR_SLACK_CHANNEL\",
\"username\": \"YOUR_SLACK_USERNAME\",
\"type\": \"mrkdwn\",
\"text\": \"$slack_msg \",
\"icon_emoji\": \":harnesshd:\"
}" <+secrets.getValue("YOUR_SLACK_WEBHOOK_URL_SECRET")>
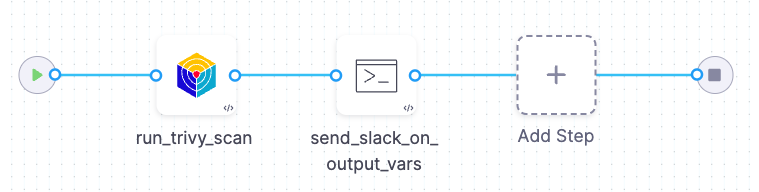
Script and pipeline examples for STO Slack notifications
Notify on scan results
This pipeline does the following:
-
Runs a Trivy scan on a container image.
-
Sends a Slack notification if the scan results include any CRITICAL, HIGH, NEW_CRITICAL, or NEW_HIGH vulnerabilities.
Full script - Try it yourself
YAML pipeline - Try it yourself
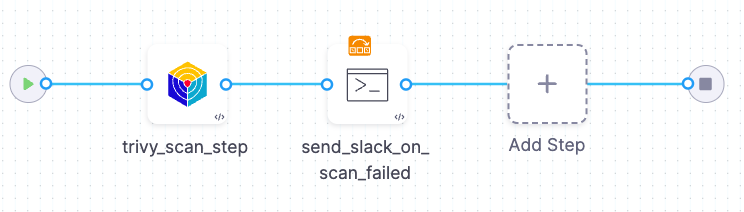
Notify when the scan step fails
This pipeline does the following:
-
Runs a Trivy scan on a container image.
-
Sends a Slack notification if the scan step fails — for example, if it exceeds the Fail on Severity threshold or violates an OPA policy.